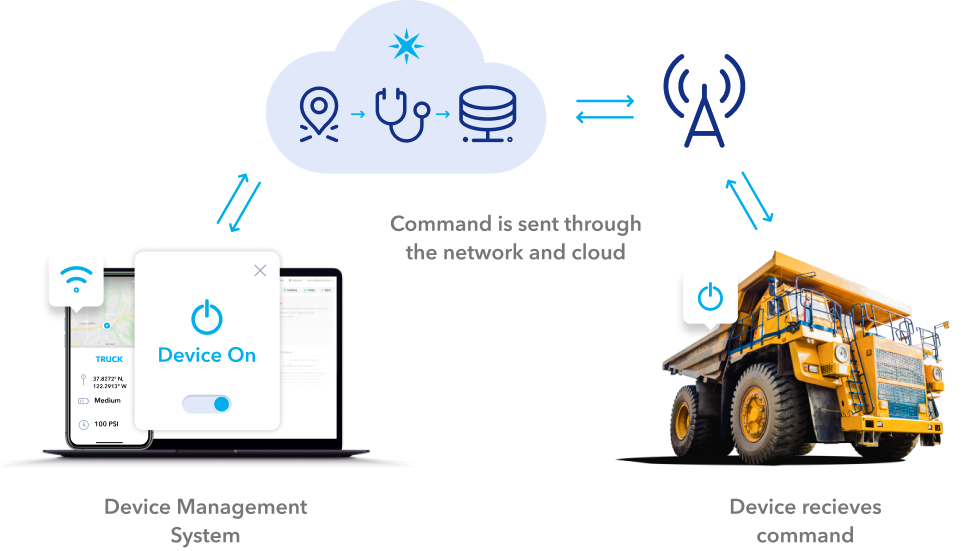
Secure Remote Management IoT Device Examples: A Comprehensive Guide
As the Internet of Things (IoT) continues to expand, secure remote management of IoT devices has become more critical than ever. Businesses and individuals alike are leveraging IoT devices to streamline operations, enhance efficiency, and improve connectivity. However, ensuring the security of these devices when managed remotely is paramount to protecting sensitive data and maintaining system integrity.
In this digital era, IoT devices are no longer limited to simple sensors or gadgets. They now include sophisticated systems that require robust security measures. Secure remote management ensures that these devices remain safe from unauthorized access, cyberattacks, and other vulnerabilities. Understanding the best practices and examples of secure remote management is essential for anyone looking to implement IoT solutions effectively.
This article will delve into the world of secure remote management for IoT devices, providing practical examples, expert insights, and actionable tips. Whether you're a business owner, IT professional, or tech enthusiast, this guide will equip you with the knowledge needed to protect your IoT infrastructure.
Read also:Rounding To The Hundredth A Comprehensive Guide For Accurate Calculations
Table of Contents
- Introduction to IoT
- Importance of Secure Remote Management
- Examples of Secure Remote Management
- Best Practices for Secure Remote Management
- Challenges in Secure Remote Management
- Tools and Platforms for Secure Remote Management
- Secure Remote Management in Enterprise Settings
- Data Security and Privacy
- Future Trends in Secure Remote Management
- Conclusion
Introduction to IoT
The Internet of Things (IoT) refers to the network of interconnected devices capable of collecting and exchanging data. These devices range from smart home appliances to industrial sensors and wearable technology. IoT has revolutionized the way we interact with technology, enabling automation, real-time monitoring, and data-driven decision-making.
One of the key aspects of IoT is the ability to manage devices remotely. This capability allows businesses to monitor and control devices from anywhere in the world, reducing the need for physical intervention. However, with this convenience comes the responsibility to ensure secure remote management to safeguard against potential threats.
Importance of Secure Remote Management
Secure remote management is crucial for maintaining the integrity and security of IoT devices. As more devices become connected, the risk of cyberattacks increases exponentially. Unauthorized access to IoT devices can lead to data breaches, system failures, and even physical harm in certain cases.
By implementing secure remote management practices, organizations can:
- Protect sensitive data from unauthorized access.
- Ensure the reliability and performance of IoT devices.
- Minimize downtime and operational disruptions.
- Comply with industry regulations and standards.
Examples of Secure Remote Management
Example 1: Cloud-Based Management
Cloud-based management is one of the most common methods for secure remote management of IoT devices. By leveraging cloud platforms, organizations can centralize the management of their IoT infrastructure, ensuring consistent security protocols across all devices.
Key features of cloud-based management include:
Read also:Iquestcoacutemo Saber Doacutende Voto Guiacutea Completa Para Encontrar Tu Centro De Votacioacuten
- Centralized device monitoring and control.
- Automatic software updates and patches.
- Real-time data analytics and reporting.
Example 2: Device Firmware Updates
Regular firmware updates are essential for maintaining the security of IoT devices. These updates often include patches for vulnerabilities and improvements to device functionality. Secure remote management ensures that firmware updates are deployed consistently and efficiently across all devices.
To ensure secure firmware updates, organizations should:
- Use encrypted communication channels.
- Authenticate devices before sending updates.
- Test updates in a controlled environment before deployment.
Best Practices for Secure Remote Management
To ensure the security and effectiveness of remote management, organizations should adhere to the following best practices:
- Implement strong authentication and authorization protocols.
- Encrypt all data transmitted between devices and management systems.
- Regularly monitor devices for suspicious activity.
- Conduct regular security audits and assessments.
- Train employees on secure remote management practices.
Challenges in Secure Remote Management
Despite the benefits of secure remote management, several challenges must be addressed. These include:
- Limited bandwidth and connectivity issues in remote locations.
- Complexity in managing a large number of devices simultaneously.
- Ensuring compatibility with diverse device types and protocols.
- Maintaining compliance with evolving security standards.
Tools and Platforms for Secure Remote Management
Tool 1: Azure IoT Hub
Azure IoT Hub is a cloud-based platform designed for secure remote management of IoT devices. It provides features such as device authentication, secure communication, and scalable device management. With Azure IoT Hub, organizations can efficiently manage their IoT infrastructure while maintaining high levels of security.
Tool 2: AWS IoT Core
AWS IoT Core is another popular platform for secure remote management of IoT devices. It offers robust security features, including device authentication, encryption, and access control. AWS IoT Core also supports integration with other AWS services, enabling organizations to build comprehensive IoT solutions.
Secure Remote Management in Enterprise Settings
In enterprise settings, secure remote management becomes even more critical due to the scale and complexity of IoT deployments. Enterprises must implement robust security measures to protect their IoT infrastructure from potential threats. This includes using advanced encryption techniques, multi-factor authentication, and continuous monitoring of devices.
Enterprises should also consider implementing a dedicated IoT security team to oversee the management and security of their IoT devices. This team can ensure that all devices are configured securely and that any vulnerabilities are addressed promptly.
Data Security and Privacy
Data security and privacy are paramount in secure remote management of IoT devices. Organizations must ensure that sensitive data collected by IoT devices is protected from unauthorized access and misuse. This involves implementing strong encryption protocols, secure data storage solutions, and compliance with relevant data protection regulations.
To enhance data security and privacy, organizations should:
- Implement data minimization practices to reduce the amount of sensitive data collected.
- Use pseudonymization and anonymization techniques to protect user privacy.
- Regularly review and update data security policies and procedures.
Future Trends in Secure Remote Management
The future of secure remote management for IoT devices is likely to be shaped by emerging technologies and trends. Some of these include:
- Artificial intelligence and machine learning for predictive maintenance and threat detection.
- Edge computing to reduce latency and improve real-time decision-making.
- Blockchain technology for secure and transparent data management.
- Quantum computing for advanced encryption and security protocols.
Conclusion
Secure remote management of IoT devices is essential for ensuring the security and efficiency of IoT infrastructure. By understanding the best practices, challenges, and tools available, organizations can implement effective remote management strategies that protect their devices and data.
We encourage readers to take action by reviewing their current remote management practices and exploring the tools and platforms discussed in this article. Additionally, please feel free to share your thoughts and experiences in the comments section below or explore other articles on our website for more insights into IoT security and management.
Remember, the future of IoT depends on our ability to secure and manage devices effectively. Let's work together to build a safer and more connected world.
Article Recommendations